Understanding IT Hygiene in Cybersecurity
IT hygiene refers to the security protocols that ensure an organization’s digital assets are both secure and functioning optimally. Effective IT hygiene encompasses vulnerability management, security configuration assessments, updated asset and system inventories, and full insights into an organization’s operational activities.
As technological tools become more sophisticated for both cybercriminals and security experts, attack methodologies also change, varying in complexity and innovation. Cyber attackers often target organizations that have lax IT hygiene, aiming to exploit recognizable security flaws or human errors. By adopting sound IT hygiene measures, like program whitelisting and system updates, organizations can fortify their defenses against such threats.
Complete transparency about IT assets is pivotal for crafting an efficient security plan. Shadow IT elements, such as unauthorized assets, software, or user accounts, can introduce unseen vulnerabilities that attackers might exploit. Through diligent IT hygiene, organizations can address these visibility issues and thus reduce potential attack points.
Challenges of Insufficient IT Hygiene
Organizations with inadequate IT hygiene often grapple with:
- Increased risk of security breaches, leading to financial losses and reputational damage. Attackers exploit the absence of robust security measures, like subpar configuration management, to breach an organization’s defenses.
- Potential loss of vital data in cyber incidents due to backup deficiencies, affecting system availability and hampering operations.
- Unnoticed malicious activities because of missing visibility into essential endpoint processes and system data. This allows attackers to hijack genuine processes for malevolent purposes undetected.
- Risks from outdated software, operating systems, and hardware.
- Partial protection and security. Organizations relying on security tools without thorough monitoring and responsive features face elevated exposure to threats.
The Significance of IT Hygiene
Maintaining stellar IT hygiene is crucial to bolster the security, efficiency, and dependability of an organization’s IT infrastructure.
By observing sound IT hygiene measures:
- Organizations notably elevate their security stance, thanks to extensive vulnerability and patch management, ensuring malicious attacks are thwarted.
- With consistent IT hygiene, organizations can substantially shrink their exposure to threats by having a complete overview of all IT assets.
- Organizations can also satisfy regulatory mandates, industry standards, and economize by embracing robust IT hygiene. Proactive oversight and timely intervention can prevent legal penalties and the financial and reputational fallout from data leaks and cyber incursions.
Wazuh’s Role in Augmenting IT Hygiene
Wazuh, an open-source security platform, delivers combined XDR and SIEM functionalities, bolstering security across cloud-based and on-premises workloads. It provides a consolidated framework for overseeing, detecting, and signaling security anomalies across monitored endpoints and cloud tasks.
Key Wazuh features crucial for maintaining a pristine network include:
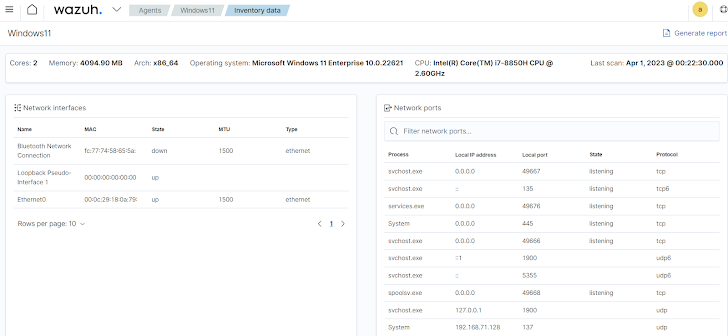
- System Inventory: Effective IT hygiene mandates real-time insights into digital assets and concurrent activities. Wazuh offers an always-current asset and system inventory, promptly flagging risks, susceptibilities, and configuration issues. This data, like a roster of open ports on endpoints, equips security personnel to spot and close superfluous ports, minimizing exposure.
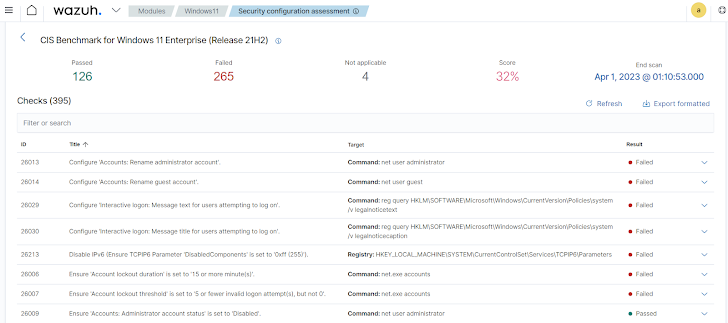
- Security Configuration Assessment (SCA): Routine configuration assessments, as per compliance guidelines, enhance security posture. Wazuh’s SCA functionality scrutinizes system settings and issues alerts when these don’t align with secure policies, ensuring compliance with standards like HIPAA, PCI DSS, NIST 800-53, and CIS benchmarks.
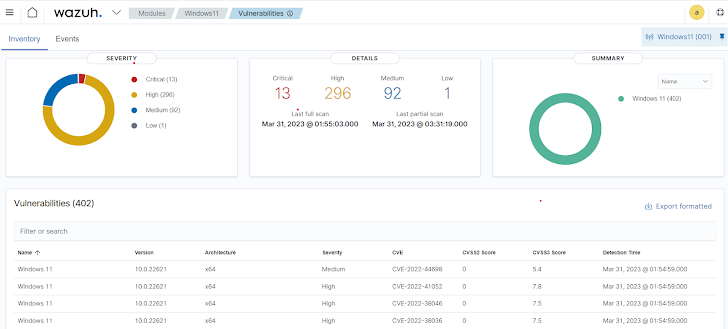
- Vulnerability Management: Proactively and consistently pinpointing and resolving vulnerabilities is integral to IT hygiene. Wazuh’s Vulnerability Detector identifies security flaws in the OS and apps on monitored endpoints, enabling swift remediation to enhance IT hygiene.
- Extended Threat Detection and Response: Wazuh’s persistent monitoring and analysis of endpoint activities in an organizational setup bolster IT hygiene. With its XDR/SIEM solution, quick detection and isolation of compromised endpoints prevent malware proliferation.
Conclusion
In the dynamic cyber threat environment of today, a rigorous IT hygiene regimen is indispensable to fend off cyber adversaries. By harnessing Wazuh‘s robust features, organizations can actively spot and counteract security threats, fortifying their cybersecurity stance.
Offered as a free, open-source SIEM and XDR tool, Wazuh amplifies an organization’s IT hygiene by alerting about potential threats, recommending remediation actions, and actively countering threats. With over 20 million yearly downloads, Wazuh enjoys broad-based support from a steadily expanding open-source community.